
loading...

Designing a verification environment for the USB with the Hub is a tedious task. It differs in various ways in comparison with a conventional Host to Device environment where the transactions are just between one or more devices directly connected with the Host. With the introduction of Hubs into the architecture, the verification environment gets more complex. As the USB supports up to 127 number of devices (including the hubs) with up to 7 tiers of Hubs in the tree structure, there is this high flexibility for the design architect to place the device at any level. Hence it is important for a verification IP for to be able configure according the design needs and more importantly having an efficient protocol monitoring system. This article focusses about how a single universal monitor can be utilized to check the transactions at any tier.
Protocol monitor plays a crucial role in any Verification IP. The sole purpose is to ensure the communication protocol is being strictly followed between any two components. In case of USB2 protocol, a monitor is placed on the bus between the host and a device as shown in Fig 1.1. Here the monitor sees the transaction between the host and that device.
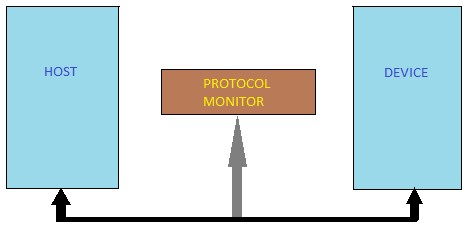
Fig 1.1
Let’s consider another architecture as shown in Fig 1.2. Here we can observe that there is a need of one monitor for each of the buses. What makes this different from the former is that the monitor on the lower tier will also see the transactions meant for the device at higher tier. For example, the host to hub1 monitor can also see the hub1 to device1 transaction. So, the logic here is to make the monitor to collect the transaction meant for the very device or the hub it has attached to and ignore the transactions meant for other device even though all the monitors here are the instances of the same monitor class.
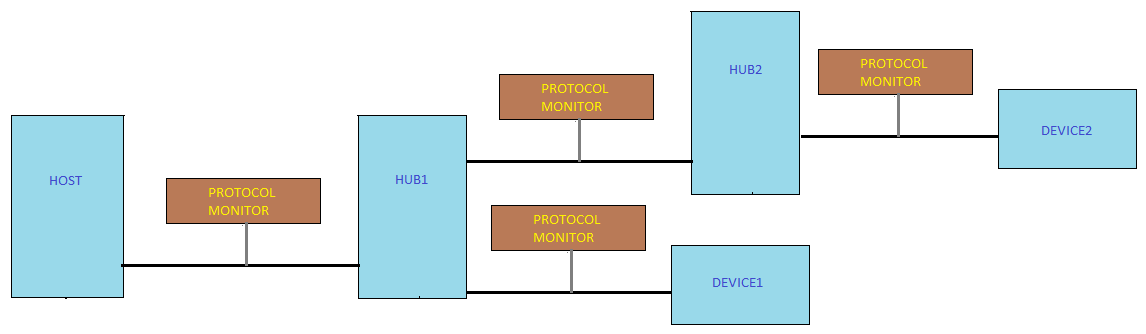
Fig 1.2
In USB2 protocol, only the token packets carry the information of the destination address. Using this field, the monitors are either prepared to expect data and handshake packets or prepared to completely ignore the entire transaction and not to flag errors as this is meant for another device. Basically the monitor is also assigned with the same address as the corresponding device/hub. This is done during the enumeration process. Thus, an SV based monitor can be instantiated any number of times at any tier and it would efficiently ensure the protocol of USB transactions.
Summary:
A single protocol monitor which has been efficiently designed with the described logic can be placed anywhere in the architecture as required by the user. This monitor plays different roles such as host to device monitor, host to hub monitor, hub to hub monitor and hub to device monitor when placed on the corresponding bus. Based on the role they have taken, the monitor checks the transactions only for that particular bus and ignores the transactions meant for different bus. Overall, this enhances the USB Verification IP to automate the instantiation of monitors during integration with the design IP as per the design needs effectively without any manual intervention